Optional API Key Enforcement for MCP Servers
We’ve introduced a new project-level security setting that allows you to require API key authentication for all MCP server requests. This opt-in feature gives you fine-grained control over who can access your MCP endpoints.
Opt-in today, default soon: This feature is currently opt-in. Starting March 1, 2026, it will be enabled by default for new organizations. We recommend enabling it now to prepare your integrations.
What’s New
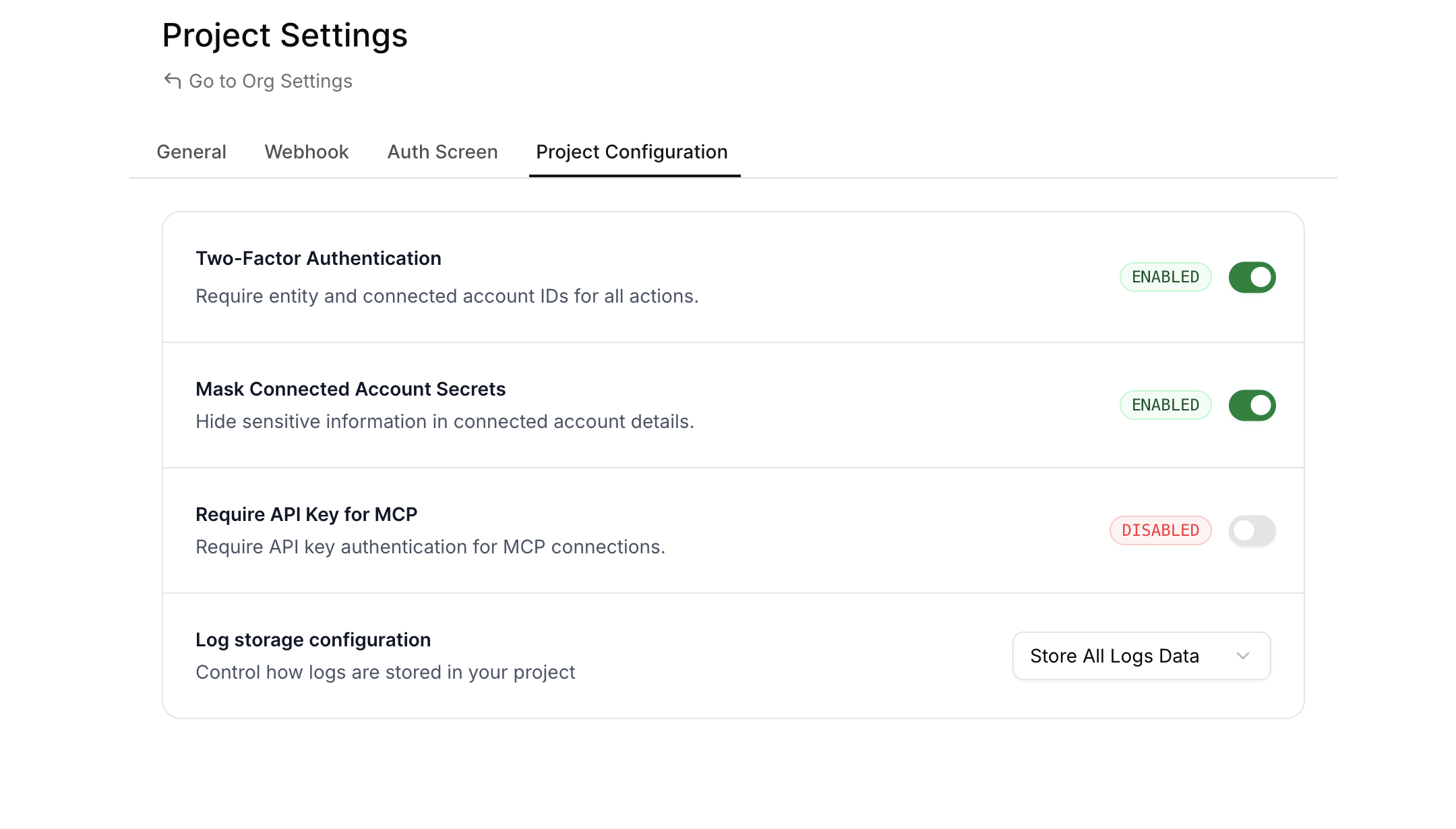
A new “Require API Key for MCP” toggle is now available in your Project Settings. When enabled, all requests to your MCP servers must include a valid Composio API key in the request headers.
How It Works
When the setting is disabled (default):
- MCP servers work without API key authentication
- Existing integrations continue to function unchanged
When the setting is enabled:
- All MCP requests must include the
x-api-keyheader with a valid Composio API key - Requests without a valid API key receive
401 Unauthorized - Only API keys belonging to the same project are accepted
Request Examples
Without API key (when enforcement is enabled):
With API key:
Enabling the Setting
Via Dashboard
- Navigate to Project Settings
- Go to the Project Configuration tab
- Find the “Require API Key for MCP” toggle
- Enable the toggle
Via API
Update your project configuration using the API:
Response:
Via Code
When to Use This
Enable API key enforcement when you need to:
- Prevent unauthorized access to your MCP servers
- Control which applications can interact with your MCP endpoints
- Add an extra security layer for production deployments
- Audit and track MCP server usage through API key attribution
API Reference
Get Current Setting
Update Setting
Consistent Error Response Structure
Tool execution errors now return a standardized response format across all failure types. Previously, the data field was empty on errors—now it always includes status_code and message, matching the structure of successful responses.
What Changed
All error responses from tool execution now include:
data.status_code: HTTP status code (ornullfor non-HTTP errors)data.message: Detailed error messageerror: Same detailed message at the top level
Before vs After
Previous error response:
New error response:
Why This Matters
- Easier parsing: Agents and code can reliably access error details from
data.messagewithout special-casing emptydataobjects - Better debugging: Detailed error messages replace generic HTTP error strings
- Consistent schema: Same response shape whether the tool succeeds or fails
Union Types Preserved in Tool Schemas
Tool schemas now use standard JSON Schema anyOf for union types, providing accurate type information for LLMs and code generators.
What Changed
Two changes affect how types appear in request/response schemas:
Toolkits with multi-type union fields (157 total)
CRM & Sales
active_campaign, apollo, attio, autobound, capsule_crm, firmao, forcemanager, gong, hubspot, instantly, intercom, kommo, leadfeeder, lever, magnetic, pipedrive, pipeline_crm, salesforce, salesforce_service_cloud, zoominfo
Marketing & Email
active_trail, beamer, delighted, dripcel, enginemailer, mailerlite, moosend, mopinion, sendspark, toneden
Communication & Collaboration
chmeetings, discord, helpdesk, helpwise, missive, slack, textit
Productivity & Project Management
basecamp, clicksend, clientary, dart, fibery, monday, notion, onedesk, productboard, rocketlane, todoist
Developer Tools & APIs
algolia, anonyflow, api_ninjas, api_sports, apify, appdrag, backendless, browserless, bubble, cloudconvert, cloudinary, cloudlayer, convertapi, databricks, datadog, datarobot, deepseek, deployhq, digital_ocean, docmosis, docugenerate, encodian, gitea, gitlab, globalping, groqcloud, hookdeck, hyperbrowser, imgbb, imgix, kibana, neutrino, npm, openai, openrouter, parsera, parseur, phantombuster, pinecone, prismic, procfu, replicate, scrape_do, serpapi, shotstack, snowflake, supabase, tavily, v0, vercel, writer, zenrows
E-commerce & Payments
brex, btcpay_server, coupa, flutterwave, gift_up, lemon_squeezy, quaderno, ramp, shopify, stripe, zoho_invoice
HR & Recruiting
ashby, bamboohr, recruitee
Data & Analytics
amplitude, census_bureau, college_football_data, currencyscoop, diffbot, ip2location, mixpanel, nasa, rosette_text_analytics, securitytrails, textrazor, twelve_data
Documents & Files
carbone, doc_certs, documenso, dropbox, excel, files_com, grist, pdf_co, share_point
Design & Media
canva, canvas, claid_ai, deepimage, heygen, metatextai
Customer Support
freshdesk, retently, servicem8, sevdesk, storeganise
Calendar & Scheduling
calendly, deadline_funnel, etermin, googlecalendar
Social Media
facebook, instagram, reddit
Location & Maps
addresszen, geoapify, google_maps, mapbox
Email Verification & Validation
clearout, icypeas, neverbounce, zerobounce
Other Integrations
bitwarden, canny, cardly, castingwords, confluence, formdesk, getform, habitica, headout, highergov, jira, keen_io, landbot, moonclerk, one_drive, outlook, googlesheets, resend, ritekit, sms_alert, tapfiliate, thanks_io, uptimerobot
Before vs After
For example, the GOOGLECALENDAR_GET_CURRENT_DATE_TIME request schema changes:
Previous (only a single type):
Now (Union types preserved):
Similarly, nullable fields like page_token in GOOGLECALENDAR_LIST_CALENDARS:
Previous:
Now:
Why This Matters
- Accurate schemas: LLMs and code generators see the full set of allowed types
- Better validation: Input validation can now correctly accept all valid types, not just the first one
Deprecating BEARER_TOKEN auth scheme for 19 toolkits
We’ve deprecated the BEARER_TOKEN auth scheme for the following 19 toolkits:
AirtableDiscordDiscordbotGmailGoogle ClassroomGoogle Search ConsoleGoogle CalendarGoogle DocsGoogle DriveGoogle SlidesGoogle SuperInstagramNtfySapling AISlackSlackbotTawk ToTikTokTwitter
Recommendation
For these toolkits, we recommend using alternative auth schemes (for example, OAUTH2, API_KEY, or other toolkit-supported schemes) instead of BEARER_TOKEN.
Backward compatibility (explicit)
This change is fully backward compatible:
- Existing auth configs and connected accounts created with
BEARER_TOKENwill continue to function. - Creating new auth configs and connected accounts with
BEARER_TOKENwill continue to work (e.g., via API/SDK). - To discourage new usage,
BEARER_TOKENauth configs / connected accounts will not be displayed in the UI for these toolkits.
Binary Data Support for Proxy Execute
The /api/v3/tools/execute/proxy endpoint now supports binary data for both file uploads and downloads.
File Uploads (binary_body)
To upload a file via the proxy, use the binary_body field in your request payload. This supports two approaches: specifying either a URL pointing to the file or providing the base64-encoded content directly.
Upload File via URL
Upload File via Base64 Content
Supported up to 4MB file size.
File Downloads (binary_data)
When the proxied request returns a binary response (for example, a PDF or image), the proxy automatically uploads the file to temporary storage, and you receive a signed URL in the binary_data field. This enables you to download large files securely.
File Download Request
File Download Response
Summary
We’d love your feedback on the new proxy execute capabilities. If anything feels unclear or you have suggestions for improvement, please reach out.
Lookahead Announcement
We’re introducing Webhook Payload V3 - a redesigned webhook structure that follows industry standards and provides better developer experience. This update affects how you receive trigger events via webhooks and Pusher.
What’s Changing?
New Webhook Structure
We’re adopting the Standard Webhooks specification for better consistency and reliability.
Headers
A new header will identify the webhook version:
Payload Structure
The payload structure is being reorganized to separate Composio metadata from trigger data:
Before (V2):
After (V3):
Key Improvements
- Metadata Separation: Composio-specific fields (connection IDs, trigger IDs, user IDs) are now in a dedicated
metadataobject - Clean Data: The
datafield now contains only the actual trigger payload without infrastructure metadata - Standardized Type Field: The
typefield now follows a consistent format (composio.trigger.message) instead of trigger-specific names likegmail_new_gmail_message - Trigger Slug in Metadata: The trigger slug (e.g.,
GMAIL_NEW_GMAIL_MESSAGE) is now available inmetadata.trigger_slugfor easy identification - Standards Compliance: Follows Standard Webhooks specification for better interoperability
- Consistent Structure: Same payload structure for both webhooks and Pusher channels
Migration Guide
Updating Your Webhook Handlers
If you’re accessing Composio metadata fields, update your code:
Checking Webhook Version
You can detect the webhook version from headers:
Rollout Timeline
- December 2025: V3 released, opt-in via project settings
- February 15, 2026: All new organizations will default to V3
- Existing organizations: Continue using V2 by default, can opt-in to V3 anytime
How to Opt-In
- Go to your project settings in the Composio dashboard
- Navigate to the Webhooks section
- Select “Webhook Payload Version: V3”
- Update your webhook handlers to use the new structure
- Test thoroughly before enabling in production
Organizations created before February 15, 2026 will remain on V2 by default. You can switch to V3 at your convenience.
Organizations created on or after February 15, 2026 will use V3 by default.
Benefits
- Better DX: Clear separation between metadata and actual trigger data
- Standards Compliance: Follows industry-standard webhook specifications
- Consistency: Same structure across webhooks and Pusher channels
- Future-Proof: Built on established standards for long-term compatibility
Need Help?
If you have questions about migrating to V3 or need assistance:
- Join our Discord community
- Check our documentation
- Contact support at support@composio.dev
Authentication & Configuration Updates Across Multiple Toolkits
Summary
This release includes significant authentication and configuration improvements across 16+ toolkits. The changes standardize Base URL handling, modernize authentication methods, and fix various endpoint configurations to improve reliability and flexibility.
Breaking Changes
We verified that active usage for these toolkits is practically zero before proceeding with these changes.
Make Toolkit
- Removed Region field in favor of explicit Base URL configuration
- Users must now provide the full Base URL instead of selecting a region
- This change provides more flexibility for custom deployments and regional endpoints
Bubble Toolkit
- Removed Subdomain field and restructured Base URL handling
- Users must now provide the complete Base URL instead of just the Subdomain
- This change standardizes URL configuration across all toolkits
Deprecated Features
HelloBar Toolkit
- Bearer authentication is now deprecated
- While still functional, users are encouraged to migrate to newer authentication methods
- Support for bearer tokens will be removed in a future release
FormSite Toolkit
- Bearer authentication deprecated in favor of API key authentication
- New integrations should use API key authentication for improved security
- Existing bearer token implementations will continue to work but should be migrated
Improvements & Fixes
Configuration Improvements
Linear Toolkit
- Base URL is no longer a configurable field
- The toolkit now uses a fixed endpoint, simplifying the authentication process
Kibana Toolkit
- Removed the default value for Base URL, allowing for more flexible deployment configurations
- Users can now specify custom Kibana instances without overriding defaults
Gong Toolkit
- Added a sensible default value for Base URL to simplify initial setup
- New users can connect without manually configuring the endpoint
Insightly Toolkit
- Added default value for the Pod field to streamline configuration
- Reduces setup complexity for standard deployments
ClickUp Toolkit
- Fixed the Base URL field type for proper validation and handling
- Ensures consistent URL formatting across all operations
Dynamic Endpoint Updates
Brilliant Directories Toolkit
- Implemented dynamic Base URL resolution for the Get Current User Endpoint
- Automatically adapts to different deployment environments
Braintree Toolkit
- Updated configuration to use production defaults
- Implemented dynamic endpoint resolution for better environment handling
- Improved reliability for production deployments
Auth0 Toolkit
- Replaced hardcoded endpoints with dynamic tenant-based URL resolution
- Supports multi-tenant deployments without manual configuration
- Automatically constructs the correct endpoint based on the tenant configuration
Endpoint Fixes
DataScope Toolkit
- Fixed the Get Current User Endpoint to use the correct API path
- Resolves authentication verification issues
D2L Brightspace Toolkit
- Updated the Get Current User Endpoint to match the latest API specifications
- Ensures proper user identification and session validation
Migration Guide
For toolkits with breaking changes, please update your configurations as follows:
- Make: Replace Region with the full Base URL (e.g.,
https://us-east-1.make.com) - Bubble: Replace Subdomain with the full Base URL (e.g.,
https://myapp.bubbleapps.io)
For deprecated authentication methods:
- HelloBar & FormSite: Generate new API keys from your account settings and update your authentication configuration
Authentication Updates Across Multiple Toolkits
We’ve updated authentication configurations for several toolkits to improve security, fix issues, and support additional deployment options.
Summary
Breaking Changes
These toolkits had incorrect or outdated authentication configurations that needed fixing. We verified that active usage for these toolkits is practically zero before proceeding with these changes.
Impact: Existing connections will stop working. You’ll need to create new auth configs and ask affected users to reconnect.
Make
Replaced region-based configuration with full base URL input. Users now provide the complete Make instance URL (e.g., https://us2.make.com or https://us1.make.celonis.com) instead of just a region code.
Recall AI
Updated from region-based to full base URL configuration. Fixed field descriptions and metadata. Updated categories to AI/Productivity/Communication and added proper documentation links.
Relevance AI
Simplified authentication by removing deprecated Project ID field. Added conditional mapping for region codes to API subdomains (AU→f1db6c, EU→d7b62b, US→bcbe5a). Region field now defaults to US.
SmartRecruiters
Fixed OAuth configuration with correct SmartRecruiters endpoints. Added proper default scopes for candidates, jobs, and users. Enabled PKCE and added refresh token support.
Deprecated (Still Working)
These changes introduce new auth methods while keeping old ones functional:
Ashby
Added new API Key authentication scheme with automatic base64 encoding and proper authorization headers.
No Action Required: Old Basic Auth method is deprecated but continues to work. Existing connections are unaffected.
Freshdesk
Added new API Key authentication scheme requiring subdomain and API key with automatic base64 encoding.
No Action Required: Old Basic Auth method is deprecated but continues to work. Existing connections are unaffected.
Freshservice
Added new API Key authentication scheme requiring subdomain and API key with automatic base64 encoding.
No Action Required: Old Basic Auth method is deprecated but continues to work. Existing connections are unaffected.
Trello
Marked Bearer Token authentication as deprecated in favor of OAuth authentication.
No Action Required: Old Bearer auth continues to function. OAuth is recommended for new connections.
ZoomInfo
Added new OAuth2 authentication scheme with comprehensive scopes for contacts, companies, audiences, scoops, news, and intent data. Deprecated the old JWT-based Basic authentication. Password field now properly marked as secret.
No Action Required: Old JWT auth continues to function. New connections will use OAuth2.
Non-Breaking Improvements
Mixpanel
Fixed region mapping logic for data residency. Added proper conditional evaluation to map regions to correct API hosts (EU, India, or Standard). Region field is now optional and defaults to Standard server. Service account secret now properly marked as secret.
No Action Required: Existing connections continue to work without changes.
Supabase
Changed base_url field type from auth_config_field to connection_field for both OAuth and API Key schemes. Updated base action logic to respect user-provided base URLs, enabling support for self-hosted Supabase instances.
No Action Required: Existing connections continue to work. Self-hosted instances now supported.
Toolkit Deprecation: Removing Empty Toolkits
What’s Changed
We’re deprecating 15 toolkits that currently have no supported actions. These toolkits will be reactivated once we add functional actions to them, ensuring you only see integrations that are ready to use.
Deprecated Toolkits
The following toolkits are now deprecated:
BREATHEHR,DIXA,EGNYTE,EXPENSIFY,FREEAGENTGUSTO,NUTSHELL,OPENNUTRITION,OYSTERHR,RAKUTENSALESFLARE,TEAMLEADER,WALGREENS,WHOOP,WIX
Impact on Your Integration
API Behavior Changes
List Toolkits Endpoint
The GET /toolkits endpoint will now exclude deprecated toolkits by default.
Need to see deprecated toolkits? Use the include_deprecated query parameter.
Backward Compatibility
Your existing integrations are safe. All other endpoints continue to work with deprecated toolkits:
- Retrieve the toolkit details
- Create auth configurations
- Manage connected accounts
- Configure MCP Servers
This ensures zero breaking changes to your current implementations.
Why This Matters
This change helps you:
- Focus on working integrations - No clutter from non-functional toolkits
- Avoid integration attempts with toolkits that have no actions
- Better developer experience with a cleaner, more actionable toolkit list
Questions?
If you have questions or need support with any deprecated toolkit, reach out to our team or check our documentation.
Toolkit Deprecation: Streamlining Our Platform
What’s Changed
We’re deprecating 60 toolkits that currently have no supported actions. These toolkits will be reactivated once we add functional actions to them, ensuring you only see integrations that are ready to use.
Deprecated Toolkits
The following toolkits are now deprecated:
ACCELO,ADOBE,AERO_WORKFLOW,AMAZON,APEX27APPOINTO,APPSFLYER,ATLASSIAN,AUTH0,AXONAUTBATTLENET,BOLDSIGN,BRAINTREE,BREEZY_HR,BREX_STAGINGBRIGHTPEARL,BROWSERHUB,CUSTOMER_IO,DEEL,DRIP_JOBSEPIC_GAMES,FACTORIAL,FITBIT,FRONT,GO_TO_WEBINARGURU,HELCIM,HIGHLEVEL,ICIMS_TALENT_CLOUD,IDEA_SCALEKEAP,LASTPASS,LEVER_SANDBOX,LEXOFFICE,MANY_CHATMBOUM,MICROSOFT_TENANT,MOXIE,ONCEHUB,POPTINPRECORO,PRINTNODE,QUALAROO,RAVENSEOTOOLS,RING_CENTRALRIPPLING,SAGE,SALESFORCE_MARKETING_CLOUD,SEISMIC,SMARTRECRUITERSTAPFORM,TERMINUS,TIMEKIT,TWITCH,VENLYVERO,VISME,WAVE_ACCOUNTING,WIZ,ZOHO_DESK
Impact on Your Integration
API Behavior Changes
List Toolkits Endpoint
The GET /toolkits endpoint will now exclude deprecated toolkits by default.
Need to see deprecated toolkits? Use the new include_deprecated query parameter.
Backward Compatibility
Your existing integrations are safe. All other endpoints continue to work with deprecated toolkits:
- ✅ Retrieve the toolkit details
- ✅ Create auth configurations
- ✅ Manage connected accounts
- ✅ Configure MCP Servers
This ensures zero breaking changes to your current implementations.
Why This Matters
This change helps you:
- Focus on working integrations - No clutter from non-functional toolkits
- Avoid integration attempts with toolkits that have no actions
- Better developer experience with a cleaner, more actionable toolkit list
Questions?
If you have questions or need support with any deprecated toolkit, reach out to our team or check our documentation.
Deprecation of is_local_toolkit Field and Removal of is_local Query Parameter
We’re cleaning up the Toolkits API by deprecating the is_local_toolkit response field and removing the is_local query parameter filter.
What’s Changing?
Response Field: is_local_toolkit (Deprecated)
The is_local_toolkit field in toolkit API responses is now deprecated. This field was originally intended to indicate whether a toolkit was local to a specific project, but it is no longer meaningful as no toolkits use this classification.
Affected Endpoints:
GET /api/v3/toolkits- List toolkitsGET /api/v3/toolkits/{slug}- Get single toolkitGET /api/v3/toolkits/multi- Get multiple toolkits
The field will continue to be returned in API responses for backward compatibility, but it will always return false. It is marked as deprecated: true in the OpenAPI specification.
Query Parameter: is_local (Removed)
The is_local query parameter filter has been removed from the following endpoints:
GET /api/v3/toolkitsGET /api/v3/toolkits/multi
This parameter was used to filter toolkits by their local status, but since no toolkits are classified as local, it served no practical purpose.
Impact on Your Code
If You’re Using the is_local Query Parameter
Before:
After:
If You’re Reading the is_local_toolkit Response Field
The field will continue to be present in responses but will always return false. You can safely ignore this field or remove any logic that depends on it.
Before:
After: